Welcome back to our comprehensive cybersecurity tutorial series.
In Part 1 we covered the basics of cybersecurity and why it's critical in today's digital landscape. Now we'll delve deeper into one of the most important aspects of personal cybersecurity: protecting your digital identity.
In this second part we will explore the different facets of digital identity protection from understanding what constitutes your digital identity to implementing robust strategies to protect it.
Understanding Your Digital Identity
Your digital identity is the sum of all digitally available information about you. It includes:
- Personal information (name, date of birth, social security number)
- Online accounts and usernames
- Email addresses
- Social media profiles
- Online shopping habits
- Browsing history
- Digital financial information
- Photos and videos you've shared online
- Comments and posts on forums or blogs
- Professional information on platforms like LinkedIn
This digital footprint is constantly growing and evolving as you interact with various online platforms and services. Protecting this identity is crucial because cybercriminals can use this information for identity theft, financial fraud, or other malicious activities.
The Risks to Your Digital Identity
Before we delve into protection strategies, it's essential to understand the risks:
- Data Breaches: Large-scale hacks of companies or organizations that hold your personal data.
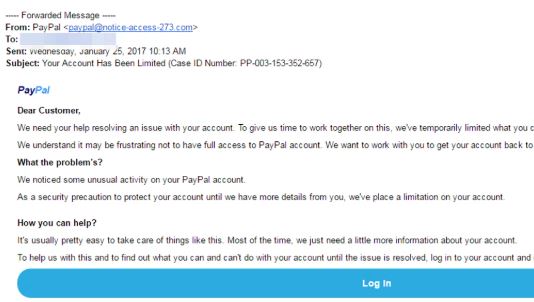
- Phishing Attacks: Deceptive attempts to obtain sensitive information by posing as a trustworthy entity.
- Social Engineering: Manipulative tactics used to trick individuals into divulging confidential information.
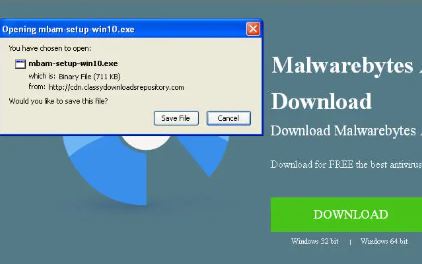
- Malware: Software designed to disrupt, damage, or gain unauthorized access to a computer system.
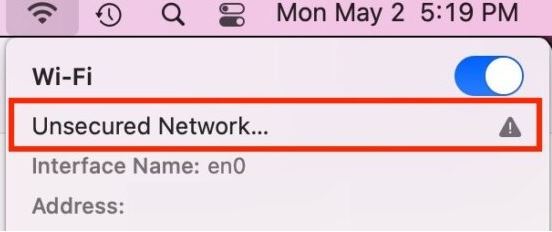
- Unsecured Wi-Fi Networks: Public Wi-Fi hotspots that can be exploited by hackers to intercept data.
- Weak Passwords: Easy-to-guess passwords that can be cracked by brute force attacks.
- Oversharing on Social Media: Providing too much personal information publicly.
Data Breaches
Large-scale hacks of companies or organizations that hold your personal data can expose sensitive information to cybercriminals. These breaches often involve unauthorized access to databases containing customer details, financial information, and login credentials. The stolen data may be sold on the dark web or used for identity theft and fraud.
Phishing Attacks
Phishing attacks are deceptive attempts to obtain sensitive information by posing as a trustworthy entity. They typically involve:
- Crafting emails or messages that appear to be from legitimate sources
- Creating urgency or fear to prompt immediate action
- Using social engineering tactics to manipulate victims
- Directing victims to fake websites designed to steal login credentials or financial data
Phishers may impersonate banks, government agencies, or well-known companies to trick recipients into revealing personal information or clicking on malicious links.
Social Engineering
Social engineering involves manipulative tactics used to trick individuals into divulging confidential information. These attacks exploit human psychology and trust to gain unauthorized access to personal information or systems. Common techniques include:
- Pretexting: Creating a fabricated scenario to manipulate victims
- Baiting: Offering something enticing to lure victims into a trap
- Quid pro quo: Promising a benefit in exchange for information
Social engineering often relies on extensive research about targets to make attacks more convincing.
Malware
Malware is software designed to disrupt, damage, or gain unauthorized access to a computer system. It can be distributed through various channels, including:
- Unsecured Wi-Fi networks
- Malicious email attachments
- Infected websites
Once installed, malware can steal personal information, encrypt files for ransom, or turn devices into parts of a botnet.
Unsecured Wi-Fi Networks
Public Wi-Fi hotspots that lack proper security measures can be exploited by hackers to intercept data. Risks associated with unsecured networks include:
- Data theft: Hackers can intercept unencrypted data transmissions
- Man-in-the-middle attacks: Attackers can position themselves between users and the connection point
- Malware distribution: Cybercriminals can spread malicious software to connected devices
Using public Wi-Fi without proper precautions can expose sensitive information to potential theft.
Weak Passwords
Easy-to-guess passwords can be cracked by brute force attacks, giving unauthorized access to accounts. Weak passwords often include:
- Common words or phrases
- Personal information like birthdates or names
- Simple number sequences
Using strong, unique passwords for each account is crucial for protecting digital identity.
Oversharing on Social Media
Providing too much personal information publicly on social media platforms can make individuals vulnerable to various attacks. Risks include:
- Identity theft: Criminals can piece together personal details to impersonate victims
- Targeted phishing: Attackers can use shared information to craft convincing scams
- Social engineering: Overshared data can be used to manipulate victims in sophisticated attacks
Being mindful of the information shared online is essential for maintaining digital privacy and security.
Strategies for Protecting Your Digital Identity
1. Practice Good Password Hygiene
The first line of defense for your digital identity is strong, unique passwords for all your accounts.
- Use long, complex passwords (at least 12 characters) with a mix of uppercase and lowercase letters, numbers, and symbols.
- Never reuse passwords across multiple accounts.
- Consider using a password manager to generate and store strong, unique passwords securely.
- Enable two-factor authentication (2FA) wherever possible for an extra layer of security.
2. Be Wary of Phishing Attempts
Phishing remains one of the most common ways cybercriminals attempt to steal your digital identity.
- Be skeptical of unsolicited emails, especially those asking for personal information or containing urgent calls to action.
- Check the sender's email address carefully for any inconsistencies.
- Hover over links before clicking to see the actual URL destination.
- Never provide sensitive information via email or on unsecured websites.
- Use anti-phishing browser extensions for added protection.
3. Secure Your Devices
Your devices are gateways to your digital identity. Keep them secure with these measures:
- Keep your operating system and all software up to date with the latest security patches.
- Use reputable antivirus and anti-malware software, and keep it updated.
- Enable device encryption on your smartphones, tablets, and computers.
- Use a Virtual Private Network (VPN) when connecting to public Wi-Fi networks.
- Set up remote wiping capabilities for your mobile devices in case they're lost or stolen.
4. Manage Your Social Media Presence
Social media platforms can be a goldmine of personal information for cybercriminals if not managed properly.
- Regularly review and adjust your privacy settings on all social media platforms.
- Be mindful of the information you share publicly, including personal details and location data.
- Avoid accepting friend requests or connections from unknown individuals.
- Be cautious about the apps and quizzes you allow access to your social media accounts.
- Consider using separate email addresses for social media and more sensitive accounts.
5. Monitor Your Financial Accounts
Financial information is a prime target for identity thieves.
- Regularly review your bank and credit card statements for any suspicious activity.
- Set up alerts for large transactions or unusual account activity.
- Use credit monitoring services to track changes to your credit report.
- Consider freezing your credit with the major credit bureaus to prevent unauthorized accounts from being opened in your name.
6. Secure Your Home Network
Your home network can be a vulnerable point of entry for cybercriminals.
- Change the default password on your router to a strong, unique password.
- Enable WPA3 encryption (or WPA2 if WPA3 is not available) on your Wi-Fi network.
- Regularly update your router's firmware.
- Consider setting up a guest network for visitors and IoT devices.
- Use a firewall to monitor and control incoming and outgoing network traffic.
7. Be Cautious with Public Wi-Fi
Public Wi-Fi networks are notoriously insecure and can be easily exploited by hackers.
- Avoid accessing sensitive accounts (like banking or email) on public Wi-Fi networks.
- Use a VPN when connecting to public Wi-Fi to encrypt your data.
- Disable automatic Wi-Fi connection on your devices to prevent them from connecting to unknown networks.
- Consider using your mobile data plan instead of public Wi-Fi for sensitive tasks.
8. Educate Yourself and Stay Informed
The landscape of cybersecurity is constantly evolving, and staying informed is crucial.
- Keep up with the latest cybersecurity news and trends.
- Learn about common scams and how to identify them.
- Attend cybersecurity workshops or webinars to enhance your knowledge.
- Share your knowledge with friends and family to help them protect their digital identities as well.
9. Use Privacy-Focused Services
Consider using services that prioritize user privacy and data protection.
- Use encrypted messaging apps for sensitive communications.
- Opt for email providers that offer end-to-end encryption.
- Consider privacy-focused search engines that don't track your search history.
- Use browser extensions that block trackers and enhance privacy.
10. Regularly Audit Your Online Presence
Periodically review and clean up your online presence to minimize your digital footprint.
- Google yourself to see what information is publicly available about you.
- Use privacy tools to request the removal of sensitive information from data broker websites.
- Delete old, unused online accounts that may contain personal information.
- Regularly clear your browser history, cookies, and cached data.
Responding to Identity Theft
Despite your best efforts, identity theft can still occur. If you suspect your digital identity has been compromised:
- Act Quickly: Time is of the essence in mitigating the damage of identity theft.
- Contact Financial Institutions: Inform your bank and credit card companies immediately.
- Place a Fraud Alert: Contact one of the three major credit bureaus to place a fraud alert on your credit report.
- File a Police Report: This creates an official record of the theft.
- Report to the FTC: File a report with the Federal Trade Commission at IdentityTheft.gov.
- Monitor Your Accounts: Keep a close eye on all your accounts for any suspicious activity.
- Change Passwords: Update passwords for all your online accounts, especially those that may have been compromised.
Conclusion
Protecting your digital identity is an ongoing process that requires vigilance and proactive measures. By implementing the strategies outlined in this tutorial you can significantly reduce the risk of your digital identity being compromised. Remember that cybersecurity is not a one-time task but rather a continuous effort to stay ahead of evolving threats.
Tips on SEO and Online Business
Next Articles
Previous Articles