In this section, we'll dive into some advanced security techniques that can help fortify your systems, networks, and applications.
As cyber threats become increasingly sophisticated, it's crucial to stay ahead with the latest defense strategies. Let’s explore some of the most effective advanced techniques to protect your digital assets.
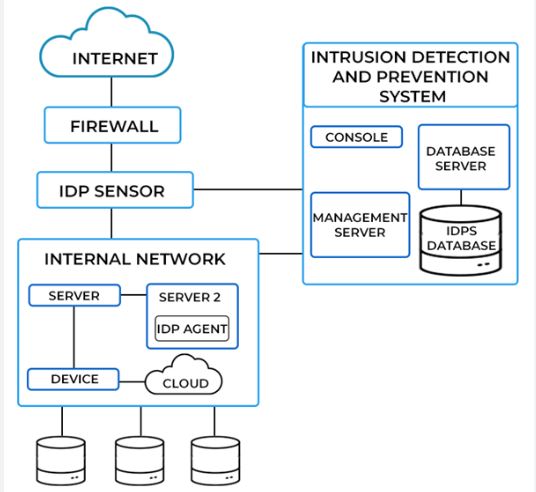
1. Intrusion Detection and Prevention Systems (IDPS)
An Intrusion Detection and Prevention System (IDPS) is a vital tool in identifying and blocking potential security threats in real-time. These systems monitor network traffic and detect malicious activities such as unauthorized access attempts or unusual data flows. While intrusion detection identifies threats, intrusion prevention also blocks them before they can harm the network.
Key features:
- Signature-based detection: Identifies known threats using predefined patterns.
- Anomaly-based detection: Detects deviations from normal network behavior, indicating potential threats.
Example: Intrusion Detection and Prevention Systems (IDPS) in Action
Let's take a look at how an Intrusion Detection and Prevention System (IDPS) might work in a real-world scenario.
Scenario: Protecting a Corporate Network from Unauthorized Access
Imagine a large corporation with a complex network infrastructure. This company handles sensitive financial data, and it's crucial to ensure that no unauthorized individuals can access its internal systems.
To protect its network, the company implements an IDPS. The system continuously monitors the network for suspicious activity.
Here’s how it operates:
1. Network Traffic Monitoring
The IDPS constantly monitors incoming and outgoing network traffic. One day, the system detects unusual behavior: an employee's workstation is sending large amounts of data to an external server. This activity is out of the ordinary, as the employee typically only accesses local resources within the company.
2. Signature-Based Detection
The IDPS checks this activity against a database of known attack signatures, which are predefined patterns of malicious behavior. The system matches the unusual data flow to a signature for a known data exfiltration attack (where sensitive information is being stolen and sent out of the network). Since it finds a match, the IDPS triggers an alert.
3. Anomaly-Based Detection
In addition to signature-based detection, the IDPS uses anomaly-based detection. It recognizes that the volume of data being transferred is much higher than what is typical for that employee’s role. This anomaly further supports the suspicion that something malicious is happening.
4. Blocking the Threat
Based on these detections, the IDPS not only sends an alert to the security team but also takes immediate action by blocking the connection between the employee's workstation and the external server. This prevents the data from being successfully exfiltrated.
5. Incident Response and Investigation
The security team investigates the situation, uncovering that the employee’s workstation was compromised by a piece of malware. The malware had been installed through a phishing email, which allowed attackers to gain access to the system. Fortunately, the IDPS detected the unusual activity before any significant damage could occur.
The security team then begins containment procedures, including isolating the affected workstation, removing the malware, and conducting a thorough investigation to determine how the attacker gained initial access.
2. Advanced Encryption Techniques
Encryption is a cornerstone of cybersecurity, ensuring that sensitive data remains secure even in transit or at rest. As cybercriminals develop more advanced techniques to bypass basic encryption, it's crucial to use stronger encryption protocols and algorithms.
- End-to-end encryption (E2EE): Ensures that data is encrypted on the sender’s side and can only be decrypted by the intended recipient, providing strong protection during transmission.
- Quantum-safe encryption: As quantum computing advances, traditional encryption methods may become vulnerable. Quantum-safe encryption techniques, such as lattice-based cryptography, aim to protect against these future threats.
Example: Advanced Encryption Techniques in Action
Let’s explore how advanced encryption techniques are applied in a real-world scenario to protect sensitive data during transmission and storage.
Scenario: Secure Financial Transactions for an Online Bank
Imagine an online banking platform that facilitates financial transactions for millions of customers. To protect customers' sensitive information, such as account numbers, passwords, and transaction details, the bank needs to implement advanced encryption techniques to ensure confidentiality, integrity, and security.
1. End-to-End Encryption (E2EE) for Transaction Data
The online banking platform uses End-to-End Encryption (E2EE) for all customer transactions. Here’s how it works in practice:
- When a customer logs into their account and initiates a transfer, their account details, amount to be transferred, and recipient information are encrypted on the customer’s device (client-side).
- The encrypted data is then transmitted over the network to the bank’s server. Because the data is encrypted, even if attackers intercept the transmission, they won’t be able to read the sensitive information.
- The bank’s server decrypts the transaction data, processes the transfer, and re-encrypts the confirmation message before sending it back to the customer’s device.
- Only the customer and the bank can decrypt the transaction details, ensuring that no third party can access the sensitive data.
This E2EE ensures that the customer’s transaction information is secure from the moment it leaves their device until it reaches its destination.
2. Advanced Encryption Standard (AES) for Data Storage
To protect stored sensitive data, such as customer account numbers and transaction histories, the bank implements Advanced Encryption Standard (AES), a symmetric encryption algorithm. Here’s an example of how it works:
- When a customer’s transaction history is saved on the bank’s database, the system uses AES-256, which is a highly secure 256-bit key length, to encrypt the data.
- Only authorized users and systems with the correct decryption key can access this sensitive information. Even if an attacker gains access to the database, they will find that the data is encrypted and unreadable without the proper decryption key.
- For example, if a hacker were to breach the bank’s database and attempt to extract data, they would find encrypted data like this:
b47ac1053d32c26d59b7ec4cae4241a3d278b5d5...– meaningless without the key.
AES encryption ensures that the sensitive customer data stored in the bank's systems remains secure even in the event of a breach.
3. Quantum-Safe Encryption for Future-Proofing
As quantum computing advances, traditional encryption techniques may become vulnerable to attacks. To future-proof their encryption methods, the bank implements quantum-safe encryption algorithms.
- The bank uses lattice-based cryptography, a type of post-quantum cryptography, to protect data from potential attacks by quantum computers.
- These algorithms are designed to be resistant to the capabilities of quantum computers, which could eventually break traditional encryption methods such as RSA or ECC (Elliptic Curve Cryptography).
By integrating quantum-safe encryption, the bank ensures that its data remains secure against both current and future threats, ensuring long-term protection as quantum computing technology develops.
4. TLS (Transport Layer Security) for Secure Communication
The bank also uses Transport Layer Security (TLS) to protect communications between its servers and customers’ web browsers. Here’s how it works:
- When a customer connects to the online banking platform via their browser, the server and the client establish a secure connection using TLS.
- During this process, the server sends its public key to the client, and the client uses it to encrypt a "shared secret" key. Both the server and the client now have a secret key they can use to encrypt and decrypt all further communications.
- This ensures that any data transmitted, such as login credentials or account details, is encrypted and cannot be intercepted or altered by attackers.
TLS is crucial for maintaining the security of data in transit over the internet, ensuring that the bank's communication with customers is encrypted and secure.
3. Multi-Factor Authentication (MFA) and Biometrics
Multi-factor authentication (MFA) adds an extra layer of security by requiring users to verify their identity using more than one method. Typically, this involves something you know (password), something you have (a device), and something you are (biometric data).
- Biometric authentication: Using fingerprint scanning, facial recognition, or voice recognition enhances security by relying on unique human characteristics, making it significantly harder for attackers to impersonate legitimate users.
Example: Multi-Factor Authentication (MFA) and Biometrics in Action
Let’s dive into a real-world example of how Multi-Factor Authentication (MFA) and biometrics work together to secure access to sensitive systems.
Scenario: Securing Access to an Online Healthcare Portal
Imagine a healthcare provider that operates an online portal where doctors, nurses, and other healthcare professionals access patient medical records. These records are extremely sensitive, so the organization must ensure that only authorized individuals can access this information. To accomplish this, they implement Multi-Factor Authentication (MFA) combined with biometric authentication.
1. Username and Password (First Factor)
The first layer of security in the portal is the traditional username and password combination. A healthcare professional logs into the system with their unique username (e.g., their employee ID) and a strong password.
- Why it's needed: The username ensures that the system knows who the user is, and the password acts as a first line of defense. However, since passwords can be stolen or guessed, it’s not enough on its own to secure sensitive medical data.
2. One-Time Password (OTP) Sent via SMS (Second Factor)
After entering their username and password, the user is prompted to enter a One-Time Password (OTP) sent to their registered phone number via SMS. This is the second factor of authentication.
- Why it's needed: Even if an attacker steals the username and password, they would also need access to the user’s phone to receive the OTP. This makes it significantly harder for unauthorized users to gain access.
3. Biometric Authentication (Third Factor)
To add an additional layer of security, the healthcare provider implements biometric authentication. After successfully entering the OTP, the user is required to use their fingerprint or facial recognition to complete the authentication process.
- Why it's needed: Biometric factors (something you are) provide a unique and difficult-to-replicate layer of security. Fingerprints and facial features are unique to each individual, so even if an attacker gains access to the user’s phone and password, they won’t be able to bypass the biometric scan.
Example: Secure Login Process
Here’s how the login process unfolds for a healthcare professional trying to access the portal:
-
Step 1: Username and Password
- The user enters their username and password.
- System checks: Is the username and password correct?
-
Step 2: One-Time Password (OTP)
- After the initial login attempt, the system sends an OTP to the user’s registered mobile number.
- User enters OTP: The system checks if the OTP matches.
-
Step 3: Biometric Verification
- After the OTP is verified, the system asks for a biometric scan (e.g., fingerprint or facial recognition).
- System checks: Is the biometric scan an exact match for the enrolled data?
-
Step 4: Access Granted
- If all three factors (username/password, OTP, and biometric scan) are verified successfully, the user gains access to the healthcare portal.
- Access is denied if any of the factors do not match or if the user fails to authenticate properly.
4. Zero Trust Architecture
The Zero Trust model operates under the assumption that no user, device, or application—inside or outside the network—is inherently trustworthy. Every access request is thoroughly verified before being granted. This approach minimizes the risk of insider threats and reduces the attack surface by constantly monitoring and validating users and devices.
Key principles:
- Never trust, always verify: Continuously verify users and devices attempting to access resources.
- Least privilege access: Ensure users only have access to the resources they absolutely need.
Example: Zero Trust Architecture in Action
Let’s explore a real-world example of how Zero Trust Architecture is implemented in a corporate environment to secure access to critical systems and data.
Scenario: Protecting a Global Enterprise Network
Imagine a global enterprise with multiple offices, remote workers, cloud-based services, and external partners. The company handles sensitive financial, employee, and customer data, which makes it a prime target for cyberattacks. In this scenario, the company adopts Zero Trust Architecture (ZTA) to strengthen its security posture, assuming that no one — whether inside or outside the network — is trustworthy by default.
1. Never Trust, Always Verify
Under a Zero Trust model, the company operates with the principle of “never trust, always verify.” This means that every access request, whether from an internal employee or an external contractor, is treated as potentially malicious until it is explicitly verified.
For example, a remote employee tries to access a company database to view customer information. Instead of automatically granting access because the employee is inside the company network (which used to be trusted in traditional models), Zero Trust requires the system to authenticate and verify the user’s identity before granting access.
2. Multi-Factor Authentication (MFA) and Least Privilege Access
As part of Zero Trust, the company implements Multi-Factor Authentication (MFA) to ensure that users are thoroughly authenticated before accessing any resource.
- MFA: When the employee attempts to log in, they are required to provide not only their username and password but also a second factor of authentication, such as a One-Time Password (OTP) sent to their phone or biometric verification (e.g., fingerprint scan). This step ensures that even if someone obtains the employee’s password, they cannot gain unauthorized access without the second factor.
Next, the system enforces Least Privilege Access, which ensures that the employee only has access to the specific data they need for their job, rather than giving them unrestricted access to the entire company network.
- Least Privilege Access Example: If the employee only needs access to customer billing data, the system restricts access to that database. The employee cannot access sensitive financial reports or HR data, even if they work in the finance department.
3. Micro-Segmentation and Continuous Monitoring
One of the core components of Zero Trust is micro-segmentation, which involves dividing the network into smaller, isolated segments. Each segment is independently secured, so even if an attacker manages to breach one segment, they cannot move laterally to other parts of the network without being detected.
- Micro-Segmentation Example: The company creates separate network segments for different departments (e.g., HR, Finance, IT) and applies strict access controls. For example, the IT team can access all network resources, but the finance team can only access financial applications and databases.
Additionally, continuous monitoring of user behavior and network traffic is implemented. This allows the system to identify any abnormal or suspicious activities, such as accessing resources that are not typically used by the employee or logging in from unusual locations.
- Continuous Monitoring Example: The system notices that the employee who usually works from the U.S. is attempting to access the database from a foreign country. An alert is triggered, and the system automatically prompts for additional authentication or blocks access altogether.
4. Device Trust and Encryption
Zero Trust also includes the verification of devices before granting access. The company ensures that only trusted devices (e.g., company-issued laptops with up-to-date security patches) can access sensitive resources. If an employee attempts to access the system from an unsecured personal device or one with outdated software, access is denied.
- Device Trust Example: If an employee’s laptop hasn’t been updated with the latest security patches, the system prevents the laptop from accessing critical databases until the required updates are installed.
Furthermore, end-to-end encryption is enforced for all data communications, ensuring that sensitive information remains protected while in transit, even if intercepted by an attacker.
5. Behavioral Analytics and Threat Detection
To enhance security, the company uses behavioral analytics to detect unusual behavior patterns. If an employee starts accessing a large amount of data suddenly or tries to access areas they don't normally use, the system will flag this behavior as a potential threat.
- Behavioral Analytics Example: The employee in this case is accessing customer billing data from multiple regions in a short time frame, which is abnormal for their role. The system alerts the security team, who can investigate the activity further.
5. Threat Hunting
While traditional security measures rely on reactive defense, threat hunting is a proactive approach where cybersecurity experts actively search for hidden threats within a network. This technique focuses on identifying and mitigating threats before they cause significant damage.
- Threat intelligence: Gathering and analyzing data on emerging threats allows organizations to stay one step ahead.
- Continuous monitoring: By maintaining constant vigilance, threat hunters can detect early signs of potential attacks and mitigate risks faster.
Example: Threat Hunting in Action
Let’s explore how Threat Hunting works in a real-world scenario and how it can proactively identify hidden threats in an organization's network.
Scenario: Detecting an Advanced Persistent Threat (APT) in a Financial Institution
Imagine a large financial institution that stores sensitive customer data, such as financial records and account details. The organization is concerned about the growing number of sophisticated cyberattacks, such as Advanced Persistent Threats (APTs), where attackers gain unauthorized access and remain undetected for extended periods, often to steal data or launch further attacks.
The organization implements a Threat Hunting strategy to actively search for potential intruders and malicious activities that may bypass traditional security measures, such as firewalls and intrusion detection systems (IDS).
1. Establishing Hypotheses and Defining the Search Criteria
The organization’s Threat Hunting Team begins by establishing a hypothesis based on potential attack vectors. For example, they suspect that a new type of malware may be infiltrating their network through phishing emails. To test this hypothesis, the team sets specific criteria to look for in their search, such as unusual email attachments, connections to known malicious IP addresses, or patterns of behavior that are not typical for legitimate users.
2. Active Search for Indicators of Compromise (IOCs)
The Threat Hunters begin actively looking for Indicators of Compromise (IOCs) — signs that an attack may have occurred or is in progress. They start by reviewing:
- Network Traffic Analysis: The team examines network logs for signs of suspicious activity, such as large data transfers to unknown external IP addresses or unusual patterns of communication between systems.
- File Integrity Checks: The team looks for any changes in critical system files that might suggest malware installation or unauthorized file modifications.
- Log Review: The hunters scrutinize event logs for signs of unauthorized login attempts, particularly those outside normal working hours or originating from unusual locations.
Through their search, they notice an anomalous pattern: several internal workstations have been communicating with an external server associated with a known cybercriminal group.
3. Identifying Suspicious Behavior (Behavioral Analytics)
Instead of relying only on predefined signatures of known attacks (like traditional IDS), the Threat Hunting team uses behavioral analytics to detect deviations from normal network behavior. They notice the following:
- Unusual User Behavior: A particular user, typically a mid-level employee, has started accessing high-value financial databases that they wouldn't normally access based on their role. Additionally, this employee's system is sending large amounts of data to an external server.
- Lateral Movement: The team discovers that a compromised workstation is attempting to move laterally across the network, trying to access other systems and escalate privileges.
At this point, the Threat Hunting team has identified a potential Advanced Persistent Threat (APT), where an attacker has gained access through phishing and is now using lateral movement to escalate their privileges and steal sensitive data.
4. Investigating and Confirming the Threat
To confirm the presence of the APT, the team begins deep-dive forensic analysis:
- Malware Analysis: They isolate and analyze the suspicious files found on the compromised systems, discovering a remote access Trojan (RAT) that allows attackers to control the systems.
- Packet Capture: They use packet capture tools to analyze network traffic between the compromised workstations and the external server, confirming that the communication is part of a data exfiltration attempt.
The team also uncovers the initial entry point: a phishing email that contained a malicious attachment, which the employee inadvertently downloaded, giving the attacker access to the workstation.
5. Mitigation and Remediation
After confirming the APT, the Threat Hunting team works with the incident response team to contain and eliminate the threat:
- Isolate Affected Systems: The compromised workstations are immediately isolated from the network to prevent further lateral movement and data exfiltration.
- Malware Removal: The team removes the RAT and any other malicious files from the affected systems.
- Password Reset and Privilege Review: They force a password reset for all affected users and review the permissions of sensitive data to ensure that only authorized personnel have access.
The Threat Hunters also work with the IT team to patch any vulnerabilities exploited by the attackers.
6. Post-Incident Analysis and Continuous Improvement
After the incident is contained, the Threat Hunting team conducts a post-incident analysis to understand how the attack occurred and improve future detection and response efforts. They:
- Update IOCs: The team updates their threat intelligence database with the new indicators of compromise and shares them with other financial institutions and cybersecurity communities.
- Improve Detection Tools: Based on the attack patterns identified, the organization refines its detection tools to better identify similar attacks in the future, particularly by adding more refined behavioral detection rules.
- Conduct Training: They also conduct employee training to raise awareness about phishing and social engineering attacks to reduce the likelihood of future successful breaches.
6. Security Automation and Orchestration
As organizations grow, manually managing security can become overwhelming. Security automation and orchestration tools help to streamline security operations, automate repetitive tasks, and coordinate responses to incidents. This enables quicker detection, response, and recovery while reducing the human error factor.
- Automated incident response: In the event of a breach, automated workflows can trigger predefined responses to contain and mitigate the attack.
- Orchestrating security tools: Integrating various security technologies allows for seamless collaboration and improved threat detection.
Example: Security Automation and Orchestration in Action
Let’s explore how Security Automation and Orchestration can be used in a real-world scenario to improve incident response and enhance security operations.
Scenario: Automating Incident Response in a Large E-Commerce Company
Imagine a large e-commerce company that handles thousands of transactions per minute, processing sensitive customer data such as credit card information, shipping addresses, and purchase history. This company faces a high risk of cyberattacks, including DDoS attacks, phishing attempts, and data breaches. To handle this, the company implements Security Automation and Orchestration (SAO) to streamline their security operations and respond quickly to incidents.
1. Automated Detection of Phishing Email
The company’s email security system is equipped with automated phishing detection tools. One day, an employee receives an email with a link that, upon inspection, is identified as a phishing attempt. Here’s how automation plays a role in the detection and response:
- Phishing Detection: The email security system automatically flags the message as a phishing attempt using AI-based threat intelligence and pattern matching techniques.
- Automated Incident Logging: As soon as the email is flagged, an incident is automatically logged in the Security Information and Event Management (SIEM) system with all relevant metadata (sender, recipient, email subject, etc.).
- Threat Intelligence Integration: The system cross-references the sender’s IP address with threat intelligence feeds to check if it’s associated with known phishing campaigns or malicious actors.
2. Orchestrated Incident Response
Once the phishing email is detected and logged, the company uses an Orchestration platform to automate the response process. The response includes multiple systems and teams working together to mitigate the risk. Here's the step-by-step orchestration process:
-
Isolate the Affected User: The orchestration platform immediately triggers a response that isolates the affected user's endpoint, preventing any potential malicious activity from spreading.
- Example: The platform sends an automated command to the Endpoint Detection and Response (EDR) tool to quarantine the employee's device from the corporate network.
-
Notify the Employee: The system automatically sends a notification to the employee who received the phishing email, warning them about the potential threat and instructing them to delete the email.
- Example: An automated email is sent to the employee, alerting them that they have received a phishing email and instructing them to take immediate action.
-
Block the URL in Network Devices: The orchestration platform automatically instructs the web proxy and firewall to block any outbound connections to the malicious URL contained in the phishing email.
- Example: The platform communicates with the firewall to create a temporary rule that blocks any traffic to the suspicious domain, preventing further potential communication with the attacker’s server.
-
Alert the Security Team: An automated notification is sent to the security operations center (SOC) team about the phishing incident, including details of the compromised email, affected endpoint, and the actions that have already been taken.
- Example: The SOC team receives a ticket in their incident management system, with all the data already populated, including the automated actions that have been executed.
3. Automated Forensic Analysis and Remediation
The system then continues to gather more information and conduct further analysis, all through security automation:
-
Automated File Analysis: The system checks whether any files attached to the email or linked to the phishing attempt have been downloaded or executed on the affected endpoint.
- Example: If any files were downloaded, the system automatically sends them for analysis to the sandboxing tool for deeper inspection to determine if the files contain malware or malicious scripts.
-
Search for Lateral Movement: Using Security Orchestration, the platform runs automated queries across the network to identify if the attacker has attempted to move laterally to other systems within the organization.
- Example: The system performs an automated search for abnormal login attempts or unauthorized access patterns across the internal network and alerts the SOC team if any suspicious behavior is detected.
-
Remediation and Patch Management: If the analysis uncovers any vulnerabilities that were exploited during the phishing attack, the orchestration platform automatically triggers remediation actions. This includes patching any exploited vulnerabilities or updating security controls.
- Example: The platform sends automated instructions to the patch management system to apply relevant patches across affected systems.
4. Continuous Learning and Updates
After the incident is resolved, Security Automation and Orchestration helps ensure that future attacks are prevented by continuously improving the organization’s defenses:
- Threat Intelligence Sharing: The system automatically updates its internal threat intelligence database with information about the phishing email and associated attack tactics.
- Example: The malicious IP address and URL are added to the organization's blocklist and shared with relevant industry threat-sharing groups.
- Automation Playbook Updates: Based on the lessons learned from this incident, the incident response playbook is automatically updated to refine response actions for similar future incidents.
- Example: The phishing detection rules are updated with new patterns and indicators, allowing the system to automatically flag more advanced phishing attempts in the future.
7. Sandboxing
Sandboxing is a security technique that involves isolating potentially harmful software or files in a controlled environment before executing them on your main system. By testing files in a “sandbox,” organizations can prevent malware from spreading or causing damage to critical systems.
Example: Sandboxing in Action
Let’s explore how sandboxing is used in a real-world scenario to detect and analyze malware in a secure and isolated environment.
Scenario: Analyzing a Suspicious Email Attachment at a Financial Institution
Imagine a financial institution that handles sensitive customer data, including personal financial records, account numbers, and transaction histories. One day, an employee receives an email that appears to be from a trusted partner with an attached file. However, the email looks slightly suspicious — the attachment is an Excel file from an unfamiliar email address.
To prevent potential threats like malware or ransomware, the organization decides to use sandboxing to analyze the file in a controlled, isolated environment before allowing it to interact with the company’s network.
1. Suspicious Email and Attachment Detection
The first step in the process occurs when the email security system flags the incoming email as suspicious based on certain criteria:
- Unusual Sender: The email comes from an email address that doesn’t match the known sender pattern of the partner.
- Attachment Type: The email includes an Excel file (.xls), which is often used in phishing and malware campaigns.
- Abnormal Subject Line: The subject line is vague and seems generic, such as “Important documents,” which is commonly used in phishing attacks.
The system automatically isolates the email, preventing it from being opened until further action is taken.
2. Sandboxing the Attachment for Malware Analysis
Instead of allowing the employee to open the file on their computer and risk infecting the network, the financial institution’s security system automatically sends the Excel attachment to a sandbox environment.
- Sandboxing Process:
- The sandbox is an isolated, virtualized environment where the attachment is executed and its behavior is monitored in real-time. The file is opened in a controlled environment that mimics the company’s actual systems, but without any risk of compromising the network.
- Execution and Observation: The sandbox begins to execute the file, allowing the malware to run in isolation. As the attachment runs, it performs various actions, such as attempting to access system files, communicate with external servers, or modify the system registry.
3. Behavioral Analysis in the Sandbox
While the file is running in the sandbox, the system monitors its behavior. Here’s what happens during the analysis:
-
Network Communication: The sandbox detects that the Excel file tries to establish a connection to an external IP address associated with a known malicious server. This is a clear indication that the file is attempting to download additional malware or send data back to an attacker.
-
File System Modifications: The file tries to make changes to system files, such as adding new executables to the directory and modifying existing files to establish persistence on the system.
-
Payload Delivery: After performing its actions, the file attempts to deliver a ransomware payload, attempting to encrypt files in the sandbox environment.
The system logs all of these activities, including the IP addresses, file modifications, and system calls, which provide key Indicators of Compromise (IOCs).
4. Automatic Response and Alerts
Based on the analysis in the sandbox, the system determines that the file is malicious and behaves like a ransomware attack. The security system takes the following actions:
-
Block the File: The sandbox immediately blocks the file from reaching any other part of the network. The file is quarantined and flagged as malicious, so it cannot be opened by any employee or system.
-
Alert the Security Team: The sandbox generates a detailed report of the file’s behavior, including all IOCs (e.g., malicious IP addresses, file names, registry changes). An alert is sent to the Security Operations Center (SOC) team with the report, allowing them to assess the situation further.
-
Update Threat Intelligence: The malicious file’s signature and the associated IP address are automatically added to the company’s threat intelligence database, which will help in identifying and blocking similar threats in the future.
5. Post-Incident Actions
Once the file is confirmed to be malware, several steps are taken to mitigate the risk:
-
Block External IPs: The firewall and network security systems are updated to block the malicious IP addresses detected by the sandbox, preventing any further communication with the threat actor's server.
-
Quarantine and Investigate Other Emails: The system scans other emails for similar attachments or suspicious patterns and quarantines any that are identified as potentially malicious.
-
Notify the Employee and Management: The employee who received the email is notified about the phishing attempt, and management is alerted to the potential threat.
-
Forensic Investigation: The SOC team conducts a forensic investigation to ensure the attack did not spread beyond the sandbox environment and that no sensitive data was exfiltrated. They also investigate any potential lateral movement attempts by the malware.
8. Advanced Malware Analysis
With malware becoming increasingly sophisticated, it’s crucial to have advanced tools and techniques for analyzing and detecting malicious software. Advanced malware analysis includes both static and dynamic analysis, helping cybersecurity professionals understand how malware operates and how to mitigate its effects.
- Static analysis: Examines the code without executing it, identifying potentially harmful patterns.
- Dynamic analysis: Observes the malware's behavior when executed, helping identify the attack vectors and potential damage.
Example: Advanced Malware Analysis in Action
Let’s walk through how Advanced Malware Analysis is used in a real-world scenario to identify, understand, and mitigate a sophisticated malware attack.
Scenario: Detecting and Analyzing a Targeted Ransomware Attack on a Healthcare Organization
Imagine a healthcare organization that manages sensitive patient data, including medical records, personal details, and insurance information. One day, the IT department notices unusual activity on the network: several files on an internal server have become encrypted, and ransom notes are appearing in multiple directories. The organization suspects that it has fallen victim to a ransomware attack, but the malware appears to be highly advanced, potentially utilizing novel techniques to evade traditional detection systems.
To fully understand and mitigate the attack, the organization’s security team employs Advanced Malware Analysis to dissect the ransomware, identify its behaviors, and develop an effective countermeasure.
1. Initial Detection and Containment
The security team first identifies the ransomware using an Endpoint Detection and Response (EDR) tool. The tool flags a suspicious executable that was recently executed on an employee’s workstation. The ransomware spreads rapidly across the internal network, encrypting critical files.
The team responds quickly to contain the attack:
- Isolate Affected Systems: The infected workstations and servers are immediately disconnected from the network to prevent further encryption and data exfiltration.
- Block the C2 Communication: The security team configures network defenses to block communication with the Command and Control (C2) server that the ransomware uses to send encrypted data and receive further instructions.
At this point, the team is ready to begin Advanced Malware Analysis to understand the ransomware’s behavior and origin.
2. Static Malware Analysis (File Analysis)
The first phase of Advanced Malware Analysis is static analysis, where the team examines the ransomware without executing it. This step helps identify key characteristics of the malware without risking further infection.
- File Properties and Metadata: The security team examines the file properties of the ransomware binary to understand its structure and possible obfuscation techniques.
- They find that the ransomware is packed with a packing algorithm, which hides the true functionality of the code. The team uses a unpacking tool to extract the original executable.
- Signature and Hash Analysis: The team calculates the hash values of the ransomware file and checks them against global threat databases like VirusTotal. They find that this variant of ransomware has not been widely recognized, indicating that it is a new strain.
- Code Review and Indicators of Compromise (IOCs): The security team manually analyzes the disassembled code using a disassembler (e.g., IDA Pro or Ghidra) to identify key functions like encryption routines, C2 communication methods, and obfuscation techniques.
The team identifies key Indicators of Compromise (IOCs), such as:
- The ransomware's unique file extensions (e.g.,
.encrypted). - Specific registry keys it creates to ensure persistence.
- The C2 server’s IP address, used to send the encrypted files.
3. Dynamic Malware Analysis (Behavioral Analysis)
The next step is dynamic analysis, where the ransomware is executed in a controlled sandbox or virtual machine (VM) environment. The goal is to observe its behavior in real-time and identify how it interacts with the system and network.
-
Execution in Sandbox: The security team runs the malware in an isolated virtual environment, ensuring it does not impact production systems. As the ransomware executes, the team observes several actions:
- File Encryption: The ransomware begins encrypting files with a complex asymmetric encryption algorithm, generating unique encryption keys for each file. It appends a
.encryptedextension to files and changes their file headers. - Data Exfiltration: The malware attempts to establish a connection to the C2 server to send encrypted files and receive further instructions.
- Registry Modifications: It adds entries to the Windows registry to ensure it will run on system reboot, establishing persistence.
- Network Traffic: The malware generates unusual network traffic, attempting to communicate with an external IP address to send encrypted files.
- File Encryption: The ransomware begins encrypting files with a complex asymmetric encryption algorithm, generating unique encryption keys for each file. It appends a
-
Behavioral Analysis Tools: Tools like Wireshark (for network traffic analysis) and Procmon (for system activity monitoring) are used to track the malware’s activity during execution. These tools reveal the ransomware’s network behavior and system changes in real time.
4. Advanced Techniques Used by the Malware
During the dynamic analysis, the team uncovers several advanced techniques used by the ransomware that help it evade detection:
- Anti-Sandboxing and Anti-Virtualization: The ransomware contains checks to detect if it is running in a virtualized environment. It scans for specific hardware identifiers or checks for the presence of sandboxing tools. If it detects a sandbox or VM, it halts execution to avoid analysis.
- Polymorphism: The ransomware’s executable code changes each time it is executed, making it harder to detect using traditional signature-based methods. This polymorphism allows it to evade detection by traditional antivirus tools.
- Encrypted Payloads: The ransomware encrypts its payload before delivering it to the infected system, making it difficult to detect until the final stages of the attack.
5. Reverse Engineering and Custom Payload Extraction
The security team performs reverse engineering to further dissect the ransomware’s functionality:
- Decryption Key Analysis: They locate the portion of the code that handles the encryption/decryption process and identify the decryption keys used by the malware. By extracting these keys, the team can reverse the encryption and restore affected files.
- Custom Payload Identification: The team identifies additional payloads that are delivered by the ransomware. These payloads are designed to perform secondary tasks, such as installing backdoors or keyloggers to facilitate future attacks.
6. Creating a Signature and Developing Countermeasures
After the analysis is complete, the security team has a comprehensive understanding of the ransomware’s behavior, techniques, and objectives. They use this information to develop countermeasures and improve overall defense strategies:
- Signature Creation: The team creates a custom signature for this variant of ransomware, which is added to the organization’s antivirus software and network security systems to detect and block future attacks.
- Update Firewalls and Intrusion Detection Systems (IDS): The team updates the organization’s firewalls and IDS to block traffic to and from the C2 server’s IP address, preventing communication between the ransomware and the attacker.
- Patch Vulnerabilities: The team identifies the initial vulnerability exploited by the ransomware to gain access (e.g., a vulnerability in an outdated software package). The vulnerability is patched across the organization’s systems to prevent future infections.
- Backup Systems Review: The healthcare institution reviews its backup systems to ensure that encrypted data can be restored from a clean backup in case of future attacks.
Tips on SEO and Online Business
Next Articles
Previous Articles